Vulnerable perimeter devices: a huge attack surface

With the increase of critical gateway devices deployed to support off-premise work, companies across the world have to adapt to a new threat landscape where perimeter and remote access devices are now in the first line.

Attack Surface Management (ASM): Examples, Software & the 4-Step
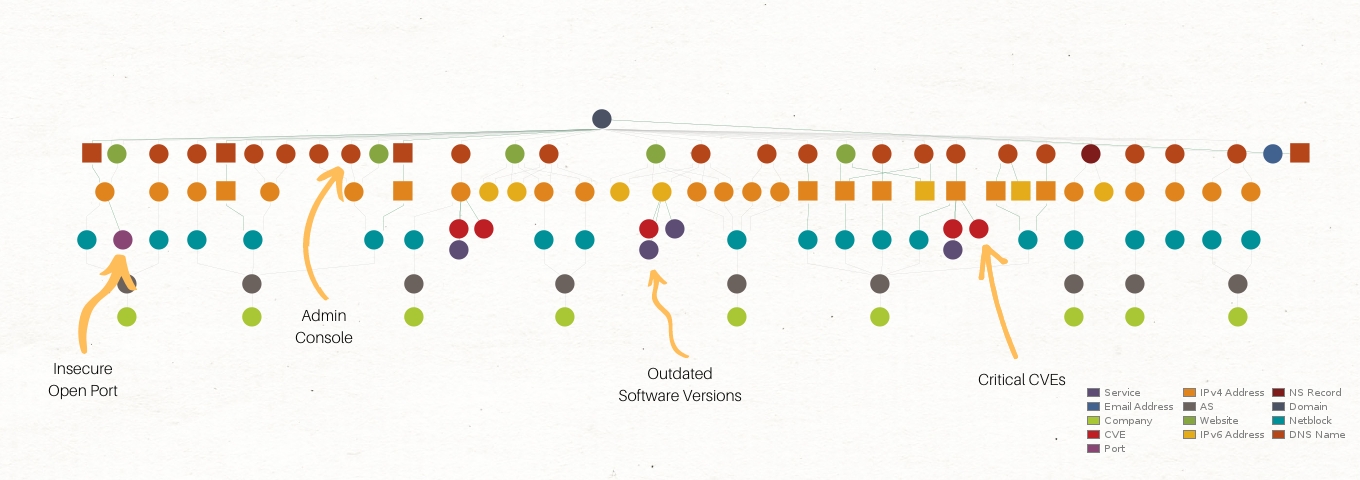
Exploring Your Attack Surface with Maltego: A Practical Guide
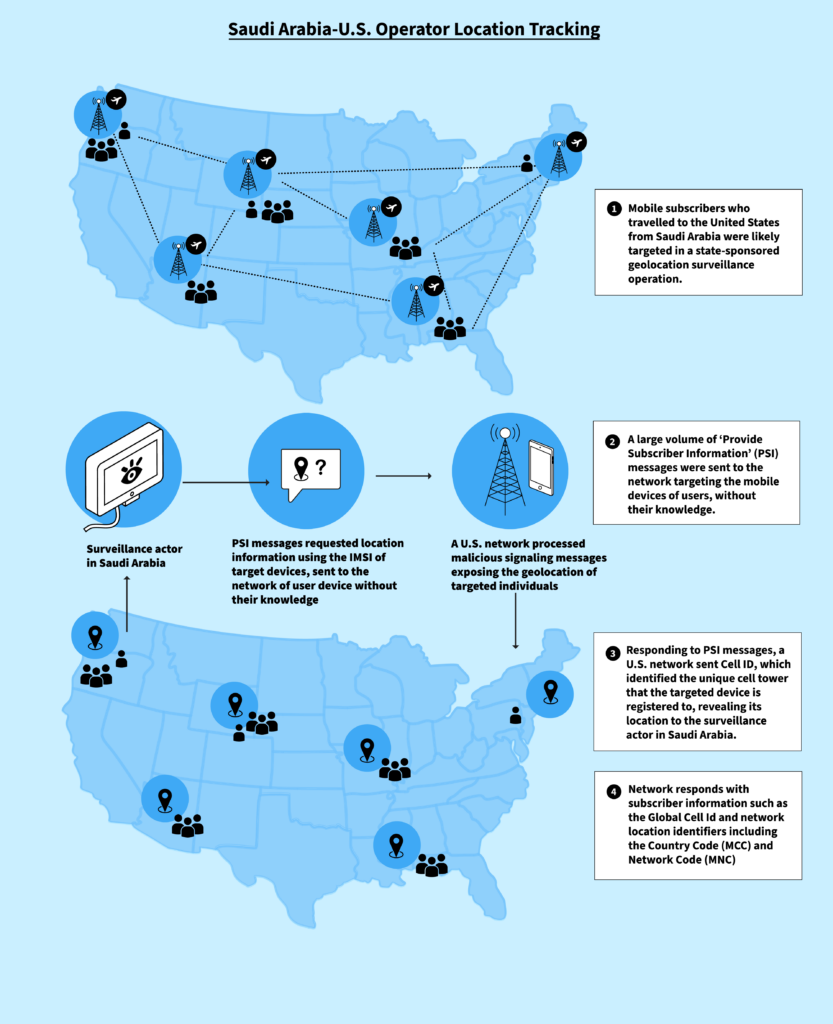
Finding You: The Network Effect of Telecommunications
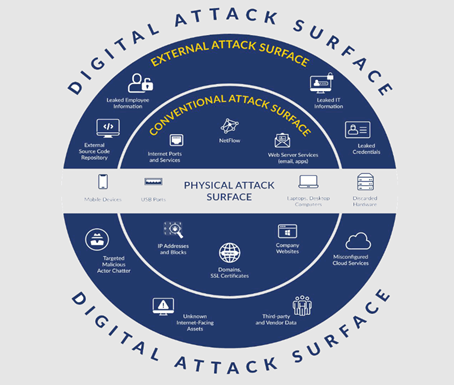
How to Reduce Your Attack Surface
What is an attack surface? Definition from TechTarget
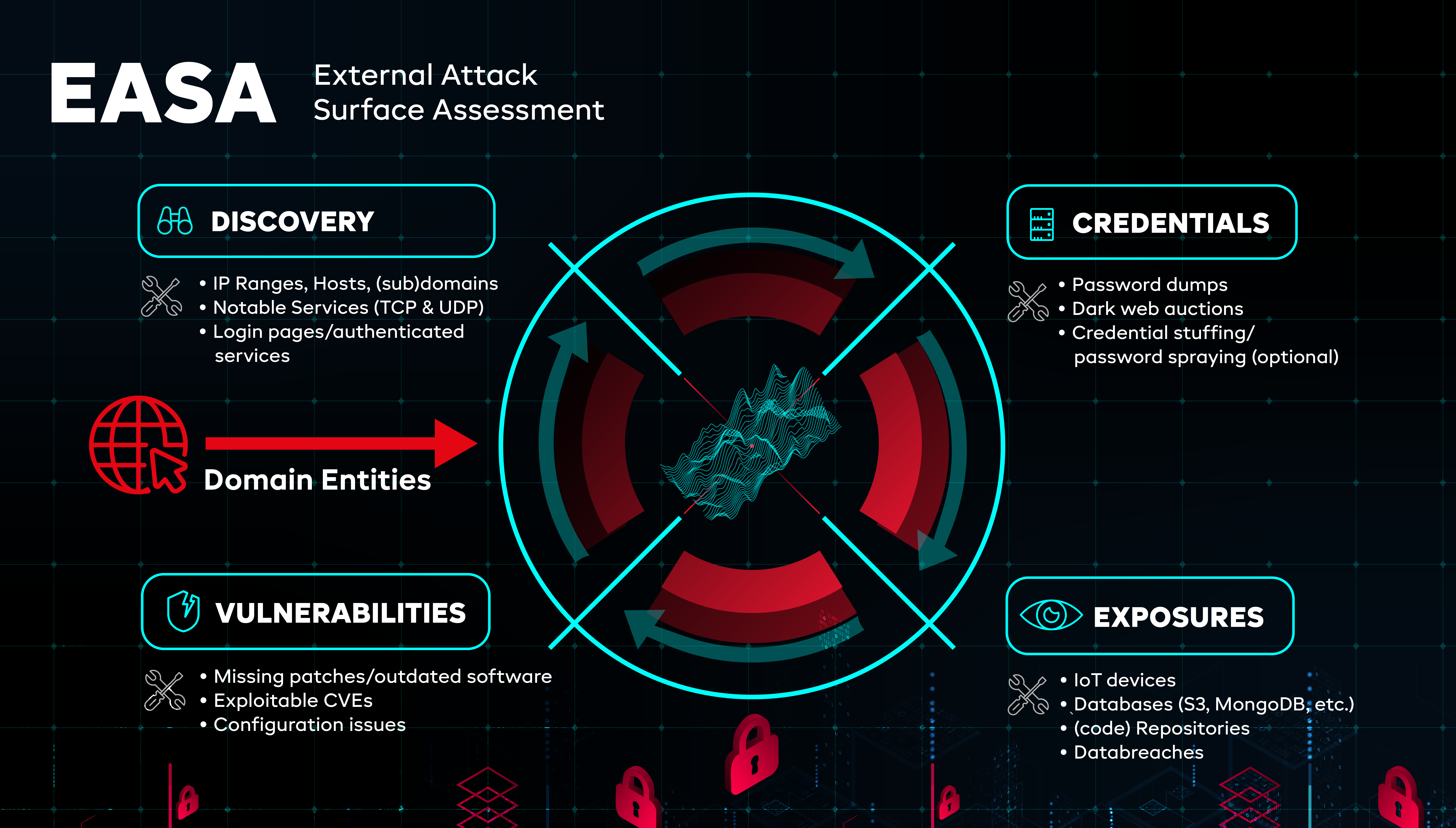
Why an External Attack Surface Assessment (EASA) is important
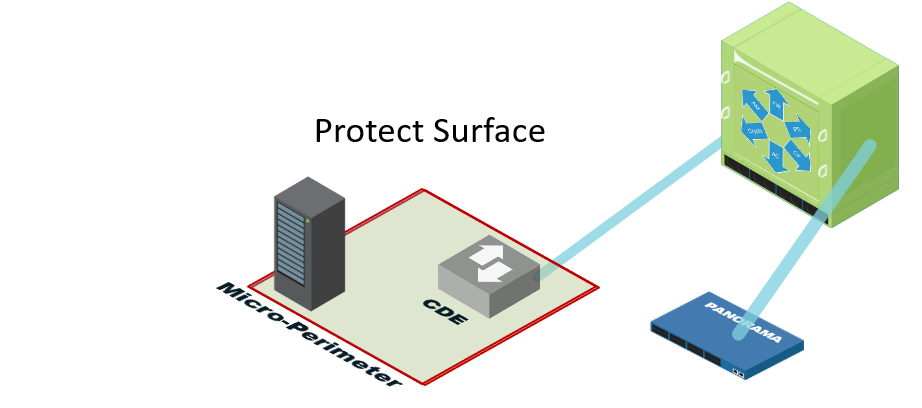
Define a Protect Surface to Massively Reduce Your Attack Surface
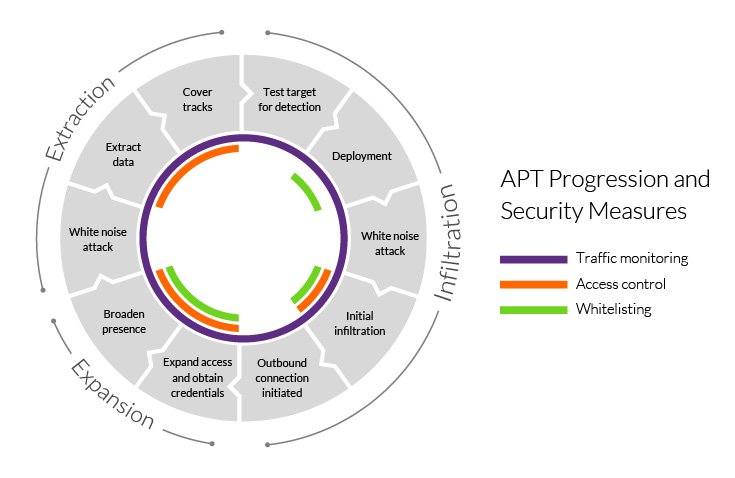
What is APT (Advanced Persistent Threat), APT Security

Viewing the profile for Ionut Ilascu
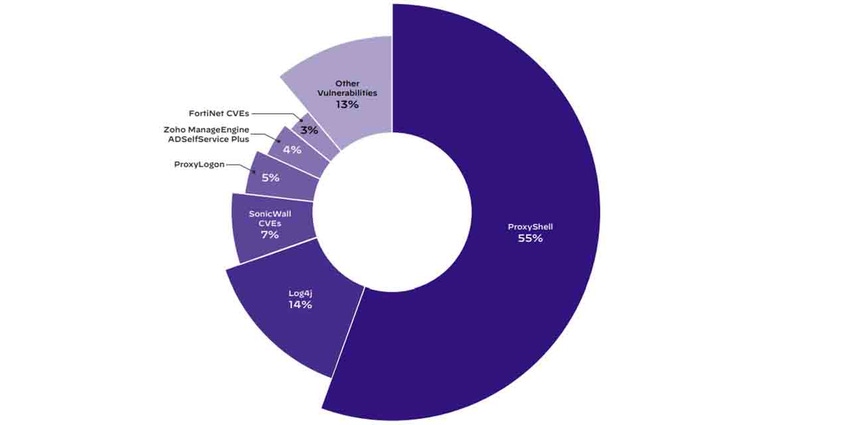
Attackers Have 'Favorite' Vulnerabilities to Exploit






