Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
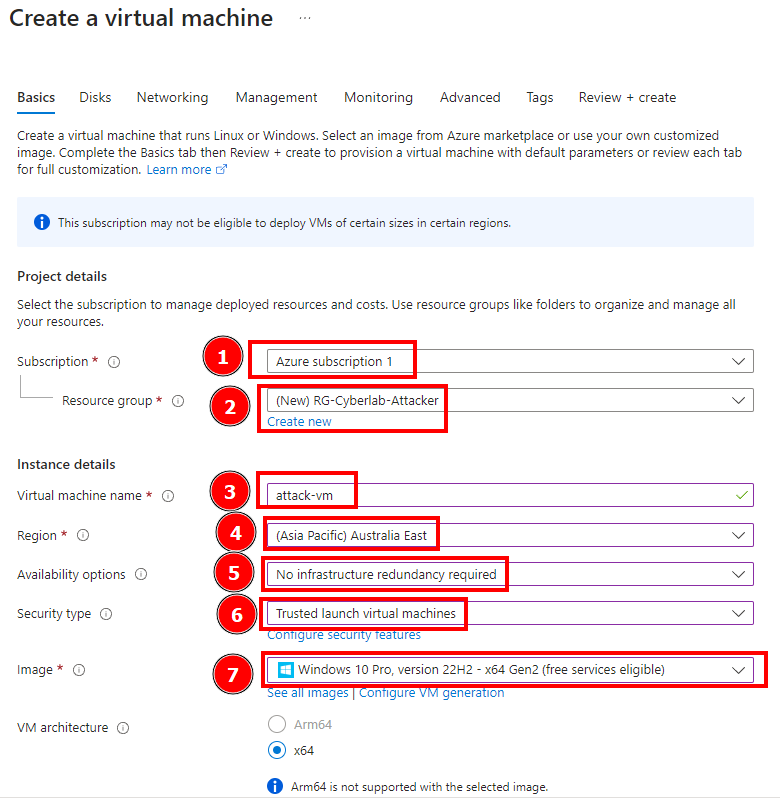
In this session we’re going to simulate an attack from another VM and then observe the attacker’s log. First we create an attacker VM. This VM’s name is attack-vm and also contain a different…

Detection, differentiation and localization of replay attack and false data injection attack based on random matrix

Detection, differentiation and localization of replay attack and false data injection attack based on random matrix

Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui

Microsoft Monitoring Agent Setup Error - Microsoft Community Hub
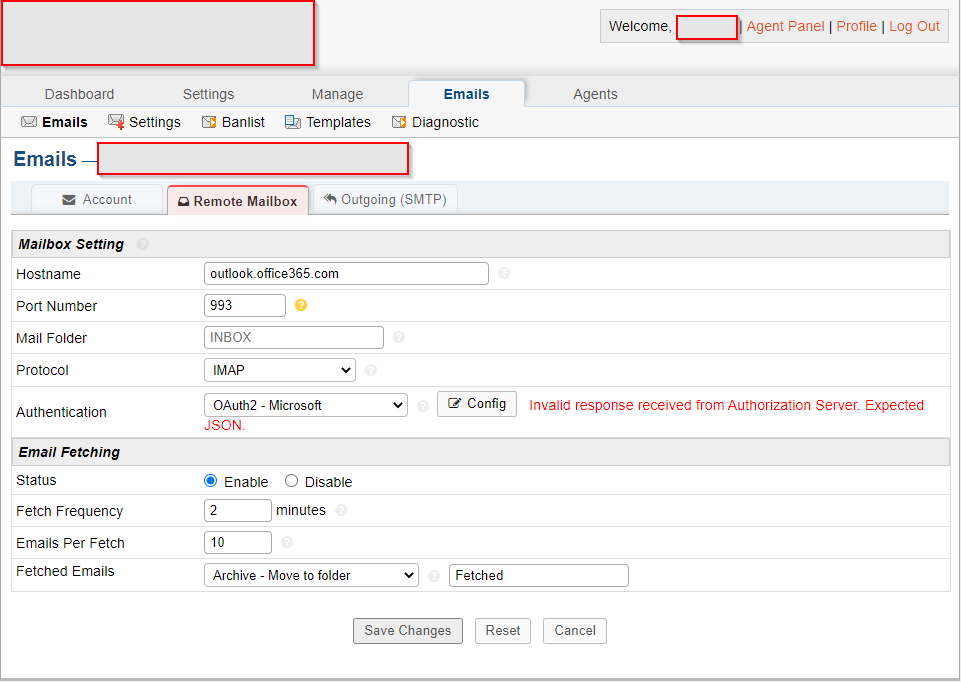
Getting an error after configuring OAuth2 - osTicket Forum

An Approach to Prevent DDoS Attack Using Real-Time Access Logs Analysis

Workflow of Failed login attempts
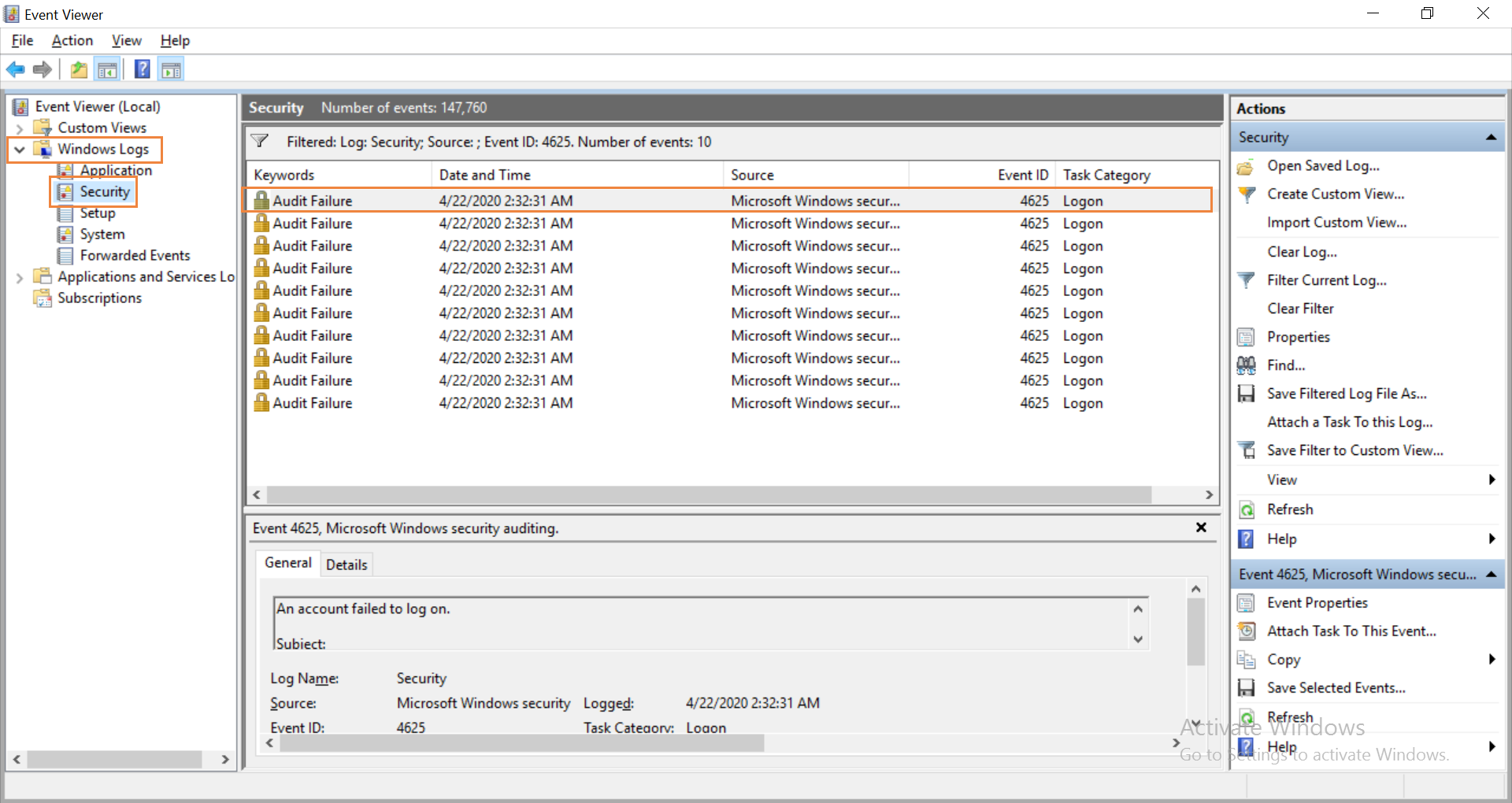
How to find the source of failed login attempts
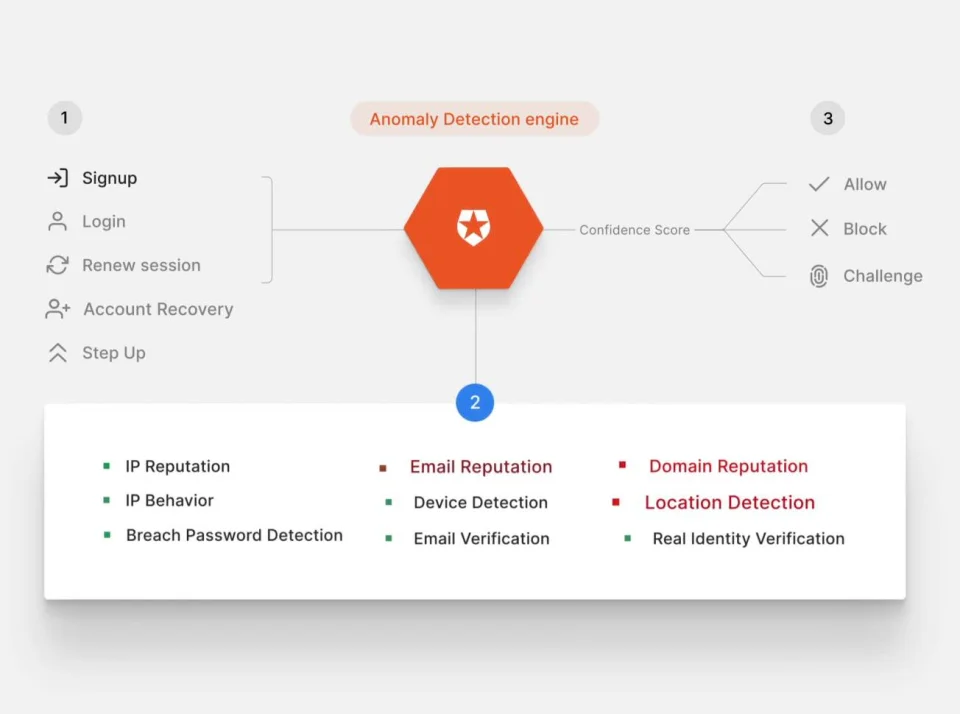
New Ways to Combat Automated Attacks: Auth0 Signals

Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui






