Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

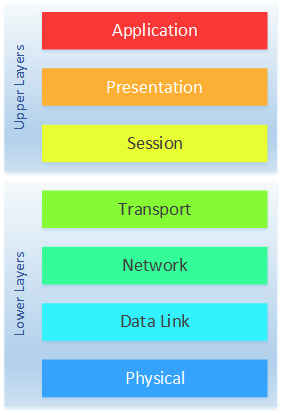
What is OSI Model? All Layers Explained With Diagram (2023)

Cyber Terrain”: A Model for Increased Understanding of Cyber Activity

Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

PDF) New Trends in Network Cyber Security (Part 1) (Paperback)

OSI Reference Model Penetration Testing

Cyber Hygiene and the Cyber Ecosystem Attack Analysis Methodology

Computer Systems Security: Planning for Success

Cybersecurity challenges in vehicular communications - ScienceDirect

The OSI model and cyber attack examples, originally published in

Seven Layers of OSI Model in an easy way

Common Security Attacks in the OSI Layer Model