Tighten SSH access to your cloud resources using short-lived SSH certificates

SSH access using public private key based authentication has several drawbacks that could potentially compromise your organization’s SSH access security. SSH certificate based authentication is a great alternative that addresses most of these security problems.

Connect by SSH tunnel or IP safelist
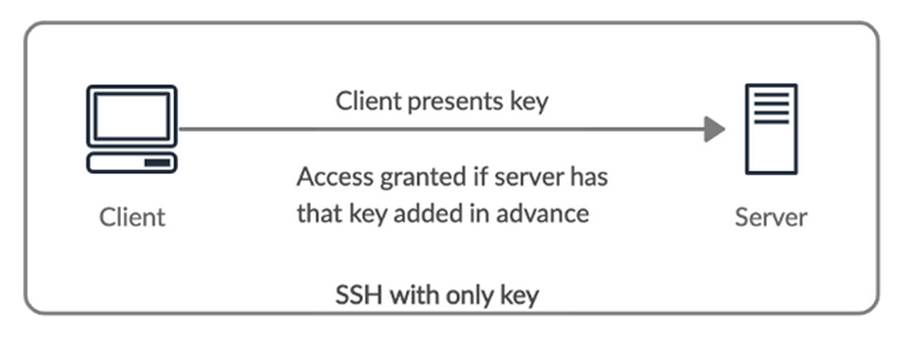
Configuring SSH Certificate-Based Authentication
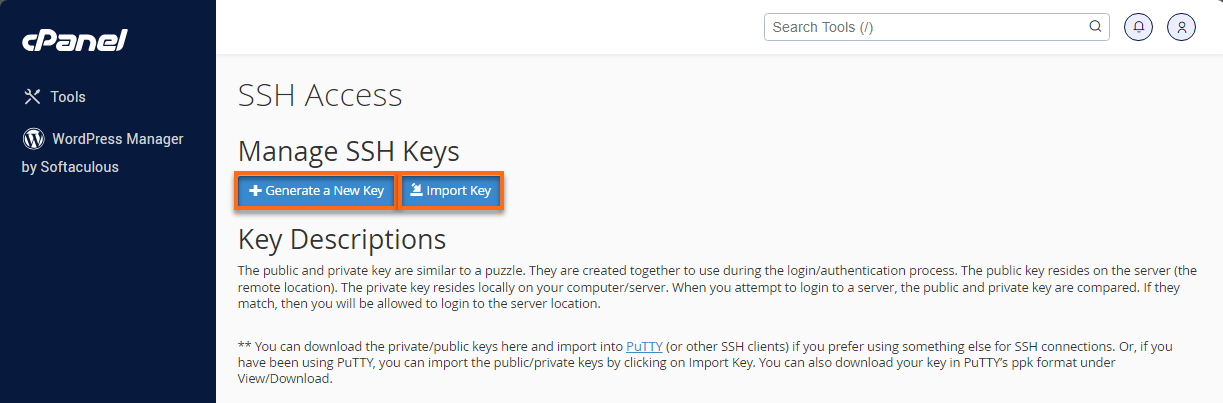
How do I Get and Use SSH Access?

Browser based SSH with Short Lived Certificates using Cloudflare

AWS Security: Bastion Host, NAT instances and VPC Peering

Network Ports in VMware Horizon

SocketXP on LinkedIn: Audit Logs: SSH session recording and replay
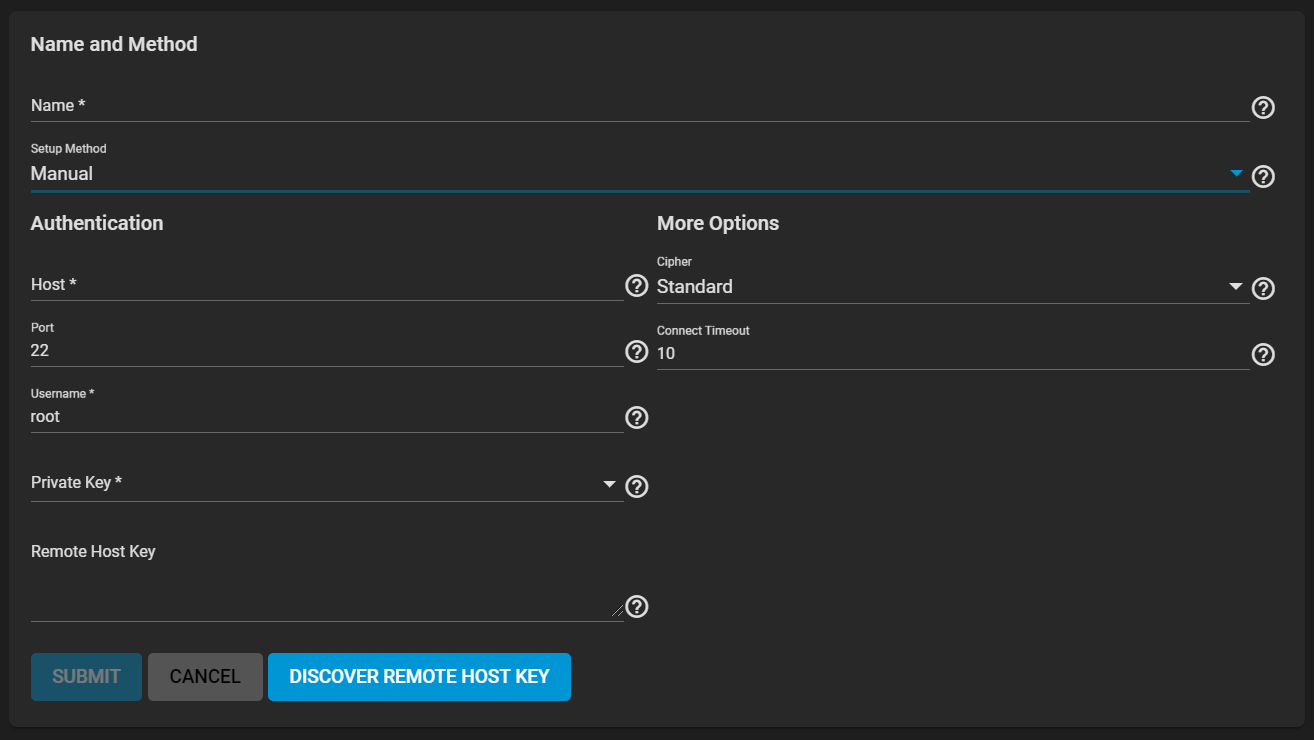
SystemSSHConnectionsAddManual.png

Useful Linux SSH Commands for Handling Files & Folders
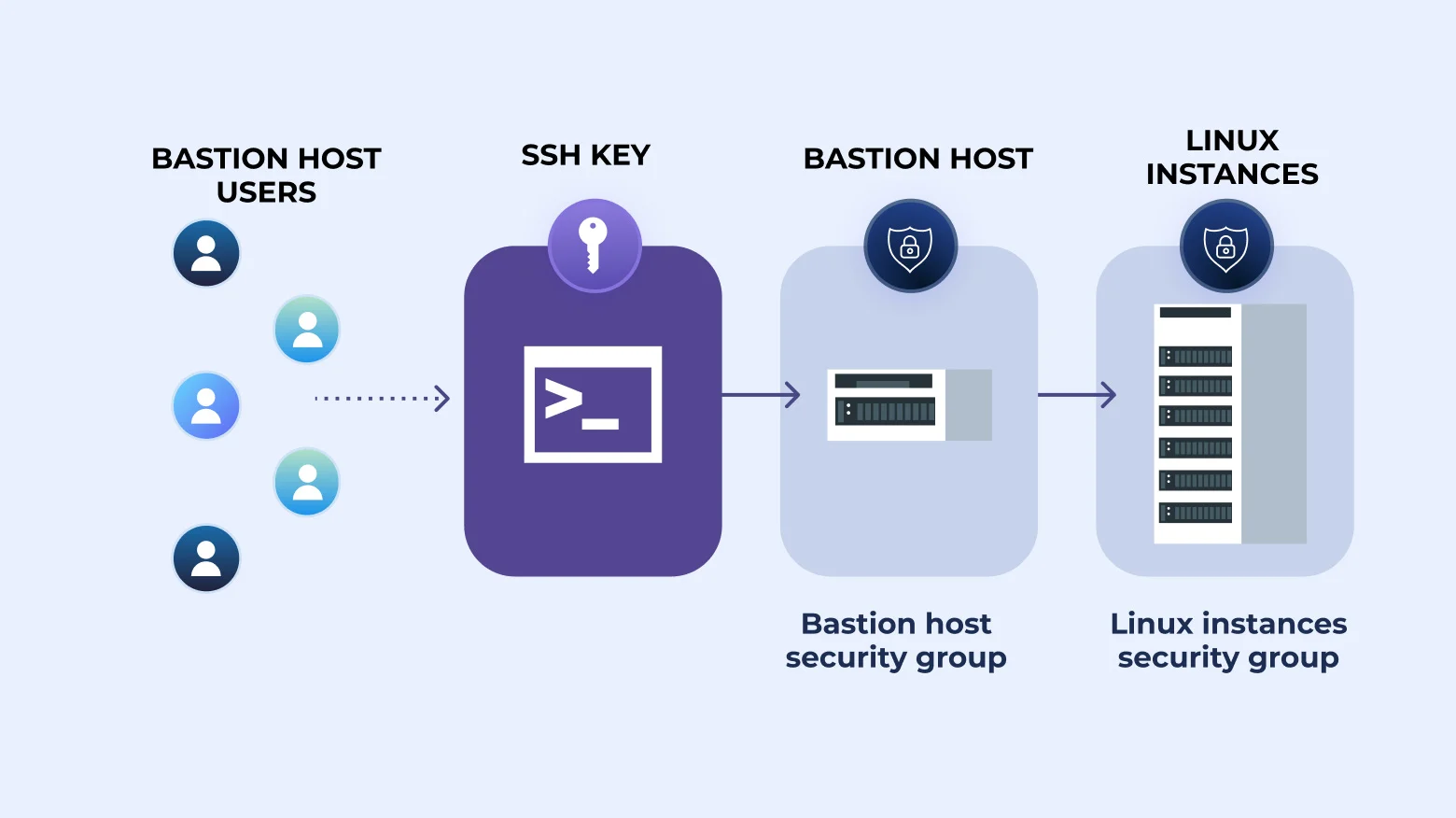
How to SSH Through Bastion With Key [Tutorial]

SSH Part 1: Configuring SSH to Securely Connect to Remote Devices

Short-Lived Certificate in Browser SSH doesn't work at all

3 Ways to Avoid Misusing AWS IAM User Access Keys
Teleport Authentication







